Are you interested in understanding how electronic payments work and why they are faster compared to traditional payment methods?
In the past, consumers had to rely on cash or checks, which required manual processing and took days to clear. However, in today’s era, we can make almost instant payments using our mobile phones. So, what factors contribute to the improved speed of payment processing in the present, considering the advancements in personal computers and the internet?
A little payment history
In the past, it was commonplace for individuals to utilize checks as a payment method at retail establishments. These physical checks featured a Magnetic Ink Character Recognition (MICR) line, which contained essential information for routing the check to the respective bank. The check would then undergo routing and clearance through one of the twelve federal reserve institutions, a process that typically took between one to three days to complete.
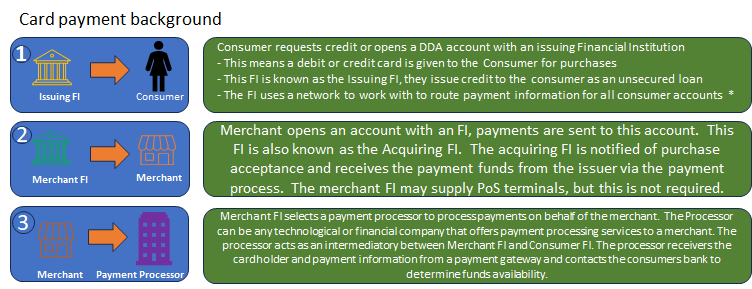
While credit and debit cards were available prior to the introduction of electronic Point of Sale (POS) readers, the ability to conduct electronic POS transactions did not emerge in the United States until the late 1970s, spearheaded by Visa. Prior to the implementation of POS readers, merchants would utilize a card imprinter to create a copy of the card and record the sales price to be charged against the customer’s account. The customer would then sign the sales slip and receive a copy as proof of payment.
It is important to note that the settlement process for card transactions differs from that of checks, as card transactions are typically settled through a network of payment processors and card issuers. Both the paper check and card imprint processes are considered outdated and cumbersome in comparison to modern payment methods.
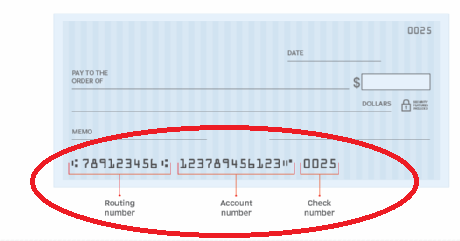
How the MICR technology works:
The check is run through a machine called a MICR reader or scanner. This machine uses magnetic sensors to read the MICR characters on the check. The magnetic ink allows the machine to accurately and quickly capture the information encoded in the MICR line. Once the MICR reader captures the information, it usually verifies the authenticity of the check, routing it to the correct bank, and processing the transaction. The MICR technology helps automate the check processing system, reducing errors, and increasing efficiency. MICR line technology on checks uses magnetic ink and special characters to encode important information. This information is then read by MICR readers or scanners to facilitate check processing and ensure accurate and secure transactions.
In the 80’s, debit and credit cards became the preferred means of payment as they were viewed as safer than carrying cash. Also, a growing number of retailers were moving toward POS readers and banks were introducing ATMs in their lobbies and retailers to alleviate customer traffic for cash transactions.
The difference between credit cards and debit cards is simply the fact that credit cards are tied to a line of credit account offered to the customer by a financial institution. When a credit card transaction is executed, the funds are pulled directly from the customer’s credit account.
Debit cards are provided by the customers FI and tied directly to the customer’s demand deposit account. Debit card transactions post to the customer’s account immediately.
The cards contain a magnetic strip, called a Magstripe, on the back of the card that contains the bank’s routing number and the customer’s account information which is used to process the payment through an encrypted message sent through the payment processor’s network.

Early on the POS systems didn’t have the capacity to store transactional information when the network was down (offline), so the merchant would revert to using a card imprinter. In the late 80’s into the 90’s, technological advances allowed for POS systems to work in offline mode. When the network is down, the POS system can store the transaction data locally on the device or in a secure internal memory. Once the network connection is restored, the system will automatically sync and transmit the stored transaction data to the appropriate backend systems for processing and settlement.
Storing transactions during network outages helps ensure that businesses can continue to accept payments and maintain a record of sales even in situations where internet connectivity is temporarily unavailable.
How the POS card reader technology works:
POS card reader technology, also known as a point-of-sale card reader, is used to process payments made with credit or debit cards. Here’s how they work. When the customer inserts/swipes/taps the card reader the card reader captures the card’s information, including the cardholder’s name, card number, expiration date, and sometimes the CVV (Card Verification Value) code.
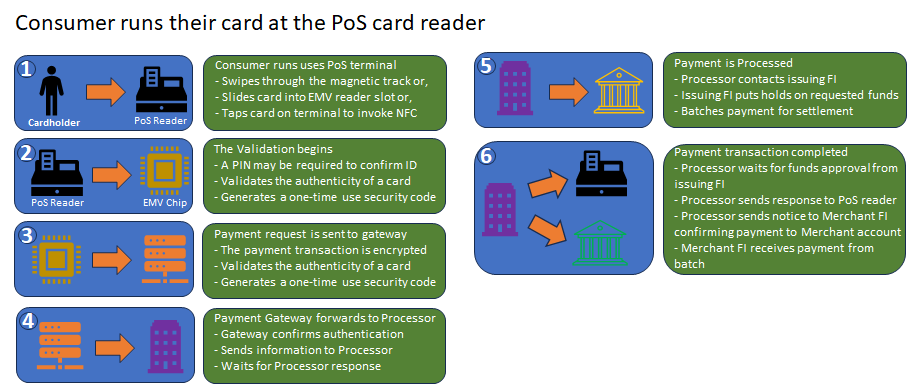
Using the captured card data, which is first encrypted to protect it from unauthorized access or interception, the card data is sent to the payment processor through a payment gateway or the card issuer’s network for authorization. The payment processor verifies the card’s validity, checks for available funds, and performs other security checks. The payment processor or card issuer’s network sends an authorization response back to the card reader.
This response indicates whether the transaction is approved or declined. If the transaction is approved, the card reader prompts the customer to complete the transaction. This may involve signing a receipt, entering a PIN, or providing a digital signature.
Once the transaction is completed, the payment processor initiates the settlement process. The funds are transferred from the customer’s account to the merchant’s account, typically within a few business days. The exact process may vary depending on the specific card reader and payment system being used.
With technical industry advances, fraudsters were able to easily steal a customer’s personal information from a Magstripe card. This made such cards very risky to use as the data is stored statically on the card giving any card reader the ability to collect bank account information from the card itself.
Because of this risk, the US banks and credit card processors moved to EMV chip enabled credit and debit cards. Such cards were available in Europe for years prior to acceptance in the U.S. Europay, MasterCard, Visa, (EMV) cards are considered a better option for secure transactions as the cardholder’s personal data on the chip is encrypted and stored on the chip and the chip be authenticated by special readers.
When a purchase is made using an EMV card, the card’s chip generates a unique encrypted token. This token contains information about the transaction and is encrypted using cryptographic algorithms. The purpose of the encrypted token is to enhance the security of the transaction by preventing the unauthorized use of the card data.
The encrypted token is sent from the card to the payment terminal, where it is then forwarded to the card issuer for verification. The issuer can decrypt the token using their cryptographic keys to validate the transaction and ensure its authenticity. By using encrypted tokens, EMV technology helps protect sensitive cardholder data and reduces the risk of fraud associated with card transactions. Shortly after the creation of the chip card, card manufacturers added near field communication, known as NFC. NFC, which is considered a subset of RFID, is also known as a tap card and contains 3 curved lines indicating the radio frequency sign.

How EMV Chip technology works:
EMV cards have a small microchip embedded in them, usually located on the front of the card. This chip securely stores and transmits the cardholder’s personal data. Unlike traditional magnetic stripe cards, EMV cards use dynamic authentication methods. This means that each time an EMV card is used for a transaction, the chip generates a unique transaction code, making it difficult for fraudsters to clone or counterfeit the card. When making a payment with an EMV card, it can be inserted into a card reader or tapped on a contactless-enabled terminal. The card reader communicates with the chip to authenticate the card and authorize the transaction.
EMV cards often require cardholder verification to further enhance security. This can be done through a PIN (Personal Identification Number) entered by the cardholder or through biometric authentication, such as a fingerprint or facial recognition. EMV technology ensures that sensitive payment data is encrypted during the transaction process. This helps protect the cardholder’s information from being intercepted or compromised. EMV cards have the ability to perform offline transactions, meaning they can securely process payments even when the card reader is not connected to the payment network. Meaning that EMV chip transactions can still process even in situations where an internet connection may be unreliable. EMV card technology enhances payment security by using dynamic authentication, encryption, and cardholder verification. It helps protect against counterfeit card fraud and provides a more secure payment experience for cardholders and merchants alike.
PayPal was launched over 20 years ago and may be considered the first Peer-to-peer network. PayPal allows its customers to set up a PayPal account with them that is normally funded through a secure site using a DDA. It also allows the user to pay or send funds from credit and debit cards to make payments on internet purchases. At its inception, PayPal was owned by and tightly coupled with eBay. It gave eBay users a way of immediately paying for auctions that they won allowing the items to be sent immediately instead of waiting on a check or electronic payment to be sent to the seller.
How PayPal works:
PayPal serves as a middleman or facilitator in financial transactions between individuals or businesses and traditional banking institutions. Instead of directly connecting to a bank account, users can link their bank accounts or credit cards to their PayPal account. When a payment is made through PayPal, it securely processes the transaction and transfers the funds between the payer and the recipient’s bank accounts, providing an additional layer of security and convenience in the payment process.
Modern P2P payment apps popped up shortly after PayPal was found to be such a huge success. They served a relatively untapped market allowing near immediate payment/transfer to another person. They also served as an alternative to using PayPal and cards, as they were especially easy to use for sending money to family and friends.
How modern P2P technology works:
Modern peer-to-peer (P2P) payment systems allow individuals to transfer funds directly to one another using digital platforms or mobile applications. In general they through the following steps:
1) User registration: The user downloads the P2P app to their mobile device. Then the user completes a form that includes personal information and a financial institution account number or credit/debit card to be used to send and receive funds.
2) After registration, the user’s identity is verified. Usually by answering a few authentication questions to ensure security and regulatory compliance.
3) Next, this is not always required, but the user usually funds the P2P account by transferring funds in from their FI account or card.
4) Payments or fund transfers are made by entering the recipient’s information and an amount to send to the recipient. Usually, a mobile number or email address, but sometimes UserID.
5) To receive the funds, the recipient must at a minimum provide routing information to their account, but may be required to set up an account on the app. Also, the recipient may have to authenticate themselves to approve the receipt of the funds. This may require a PIN, password, biometric authentication, or some other type of security measure.
6) Once complete, the P2P payment system securely transfers the funds from the sender’s account to the recipient’s account. Depending on the app, this may involve routing the transaction through the banking system or using alternative methods like digital wallets.
7) Once complete, both parties are notified of the transaction to provide confirmation that that the transfer is complete.
8) The recipient can then access the transferred funds in their P2P payment account. They can choose to keep the funds in the account for future transactions or transfer them to their linked bank account.
9) To ensure that the transaction is secure, the P2P system will employ various security measures, such as encryption, fraud detection algorithms, and transaction monitoring, to protect users’ financial information and prevent unauthorized access.
No matter which technology you use, be assured your payment will make it to your account. However, please keep in mind that some technology is much safer than others. Which is your preferred payment method?