In today’s fast-paced world, digital payments have become the go-to method for conducting transactions. Gone are the days of carrying around bulky wallets stuffed with cash or fumbling for loose change. With just a few taps on a smartphone or a click of a button on a computer, payments can be made seamlessly and securely. This article explores the world of digital payments, delving into the various benefits they offer and the technologies that power them.
Digital payments have revolutionized the way we handle financial transactions. Some key advantages are convenience, speed, security, trackability, and accessibility.
There is no need to carry physical cash or cards. All you need is your smartphone or computer, making it incredibly convenient for everyday transactions. Traditional payment methods often involve time-consuming processes such as counting change or waiting for checks to clear.
Digital payments, on the other hand, are instantaneous, allowing for quick and efficient transactions. These payment platforms utilize advanced encryption technologies to ensure the security of your financial information. This provides peace of mind, knowing that your personal data is protected.
These payments can be made anytime, anywhere, as long as you have an internet connection. Digital payment accessibility makes it easy to send or receive money across borders, fostering global connectivity. Unlike cash transactions, digital payments leave a digital footprint, making it easier to track and manage your finances.
The Technologies Behind Digital Payments
Digital payments rely on a range of technologies to facilitate seamless transactions. Let’s explore some of the key players in this space:
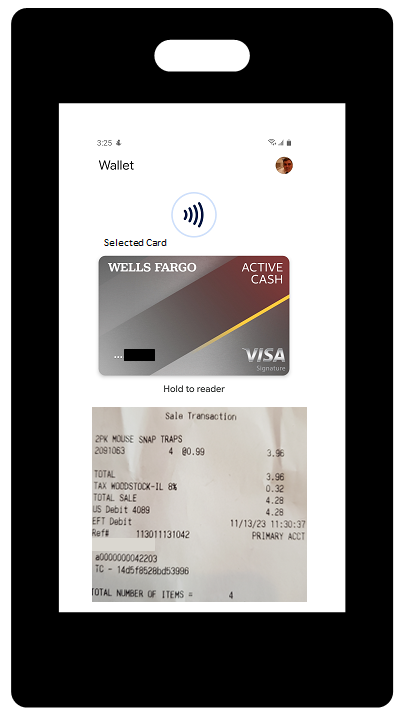
1. Mobile Wallets: Mobile wallets, such as Apple Pay and Google Pay, allow users to store their payment information securely on their smartphones. These wallets use near-field communication (NFC) technology to enable contactless payments.
How do Mobile Wallets work?
Mobile wallets work by securely storing your payment information, such as credit card or bank account details, on your mobile device. When you make a purchase, the mobile wallet app uses various technologies to facilitate the transaction.
You download a mobile wallet app from a trusted provider and create an account. During setup, you may be asked to link your payment methods by entering the card details manually or scanning the card using your device’s camera. The mobile wallet app encrypts and stores your payment information securely on your device. Some apps may also offer additional security features like biometric authentication (fingerprint or face recognition) or PIN codes to access the wallet.
When you’re ready to make a purchase, you open the mobile wallet app and select the payment method you want to use. This could be a credit card, debit card, or bank account linked to the app. Depending on the technology used, the mobile wallet app may utilize near-field communication (NFC), QR codes, or other methods to communicate with the merchant’s payment terminal.
The app generates a unique token or code that represents your payment information without sharing your actual card details. The token or code is sent to the merchant’s payment terminal, which then communicates with the relevant payment networks and your bank or card issuer to authorize and process the transaction.
Once the transaction is approved, you receive a confirmation on your mobile device, and the payment is completed. Some mobile wallets may also provide digital receipts or transaction history within the app.
2. QR Codes: Quick Response (QR) codes have gained popularity as a convenient payment method. By scanning a QR code with your smartphone, you can initiate a payment directly from your digital wallet.
How do QR Codes work?
Quick Response codes, are two-dimensional barcodes that can be scanned using a smartphone or QR code reader. They work by encoding information in a pattern of black and white squares, which can represent various types of data such as text, URLs, contact information, or even multimedia content.
When you scan a QR code using a compatible app or device, the scanner captures the image of the code and decodes the information embedded within it. This information is then processed and displayed on the screen of your device.
Once the QR code is scanned and decoded, the action associated with the encoded information is triggered. For example, if the QR code contains a URL, scanning it will open the corresponding website or webpage in your device’s browser.
3. Payment Gateways: Online businesses often utilize payment gateways to process transactions. These gateways act as intermediaries between the customer, the merchant, and the financial institutions, ensuring secure and efficient payments.
How do payment gateways work?
The customer selects products or services on the merchant’s website and proceeds to the checkout page. The customer then enters their payment details, such as credit card information or other supported payment methods, into the payment gateway’s secure payment form on the merchant’s website.
The payment gateway encrypts the customer’s payment information to ensure its security during transmission. This encryption helps protect sensitive data from unauthorized access. Next the payment gateway securely sends the encrypted payment information to the appropriate financial institution, such as the customer’s bank or credit card company.
The financial institution receives the authorization request, verifies the customer’s payment details, and checks for available funds or credit limit. It then sends an authorization response back to the payment gateway. Based on the authorization response, the payment gateway informs the merchant’s website whether the transaction is approved or declined. If approved, the payment gateway initiates the transfer of funds from the customer’s account to the merchant’s account. The customer receives a confirmation message regarding the status of the transaction, and the merchant fulfills the order or provides access to the purchased goods or services.
Throughout this process, payment gateways employ various security measures, such as encryption, tokenization, and fraud detection systems, to ensure the safety of sensitive customer data and protect against fraudulent activities.
4. Cryptocurrencies: The rise of cryptocurrencies, like Bitcoin, has introduced a new form of digital payment. These decentralized currencies utilize blockchain technology to enable secure peer-to-peer transactions without the need for intermediaries.
How do Cryptocurrencies work?
In general, Cryptocurrencies work through a technology called blockchain. A blockchain is a decentralized and distributed ledger that records transactions across multiple computers or nodes. Cryptocurrencies use cryptographic techniques to secure transactions and control the creation of new units. This encryption helps prevent the duplication or counterfeiting of digital currencies. Unlike traditional currencies, cryptocurrencies are decentralized, meaning they are not controlled by any central authority like a government or a bank. Instead, they operate on a peer-to-peer network of computers.
Transactions made with cryptocurrencies are recorded on a blockchain. A blockchain consists of a chain of blocks, where each block represents a set of transactions. This ledger is distributed across multiple computers or nodes, ensuring transparency and avoiding single points of failure. To validate and add transactions to the blockchain, cryptocurrencies rely on a process called mining. Miners use powerful computers to solve complex mathematical problems, and when they find a solution, they add the block of transactions to the blockchain. This process also ensures the security and integrity of the cryptocurrency network. Cryptocurrencies use consensus mechanisms to agree on the state of the blockchain and confirm transactions. Popular consensus mechanisms include proof-of-work (PoW) and proof-of-stake (PoS). These mechanisms prevent fraudulent transactions and maintain the overall integrity of the network.
Cryptocurrency wallets are used to store and manage digital currencies securely. Wallets can be software-based, hardware-based, or even paper-based. They contain public and private keys, which are used to sign and verify transactions. Transactions involve transferring digital currency from one wallet to another. Each transaction is recorded on the blockchain and requires the digital signature of the sender to authenticate the transfer. When a transaction is confirmed, the blockchain is updated, and the balances of the respective wallets are adjusted. This ensures that everyone in the network has an updated view of the ownership and history of each cryptocurrency unit.
Types of Digital Payments
Digital payments come in various forms, catering to different needs and preferences. Here are some popular types:
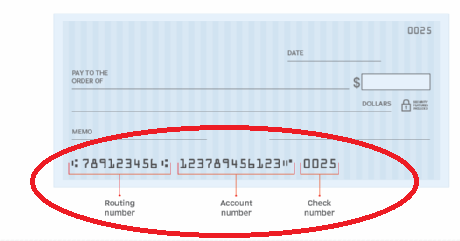
– Credit and Debit Cards: The most common form of digital payment, cards offer convenience and widespread acceptance. Credit and debit cards work as digital payment methods by allowing individuals to make purchases electronically. It’s important to note that the specific processes and systems may vary depending on the card network, issuer, and payment infrastructure used. Additionally, security measures like encryption and tokenization are employed to protect cardholder information during the transaction process.
– Virtual Cards: Virtual cards are issued online and can be used for online purchases or linked to mobile wallets for contactless payments. Virtual debit and credit cards work similarly to physical cards, but without the physical presence.
– Peer-to-Peer (P2P) Payments: P2P payment platforms, like Venmo and PayPal, allow users to send money directly to friends or family members using their email address or mobile number. Users first need to create an account and link it to their bank account or credit/debit card. Once set up, they can initiate a payment by entering the recipient’s information, such as their email address or mobile number. The platform then securely transfers the funds from the sender’s account to the recipient’s account. This transfer can occur through various methods, such as direct bank transfers, digital wallets, or even cryptocurrency transactions.
P2P payment platforms often provide additional features like transaction history, notifications, and the ability to split bills or request payments from others. Some platforms may also offer added security measures, such as two-factor authentication or encryption, to protect user information and transactions. P2P payment platforms simplify the process of transferring money between individuals, making it convenient and efficient for everyday transactions.
– E-Wallets: E-wallets, such as PayPal and Paytm, provide a secure storage solution for your financial information, enabling you to make online or in-store payments. These digital wallets utilize electronic systems to securely store and manage payment information on digital devices like smartphones or computers. Users can add funds to their e-wallets by transferring money from their bank accounts or receiving payments from others. Some e-wallets also support cash deposits or integration with other payment platforms. By securely storing payment details like credit/debit card information or bank account numbers, e-wallets eliminate the need to enter this information for each transaction, enhancing convenience for future payments.
When making a payment, users can select their e-wallet as the preferred payment method at participating merchants or online platforms. The e-wallet then securely transfers the payment information to complete the transaction.
To ensure user information and transactions are protected, e-wallets employ various security measures such as encryption, tokenization, biometric authentication (e.g., fingerprint or facial recognition), and two-factor authentication. Additionally, e-wallets often offer features like transaction history, balance tracking, integration with loyalty programs, and the ability to send or receive money from other e-wallet users.
Overall, e-wallets provide a convenient and secure means for users to make digital payments using their stored payment information.
– Online Banking: Many banks offer online banking services that enable customers to transfer funds, pay bills, and make purchases directly from their accounts.
Online banking allows individuals to access and manage their bank accounts through the internet. To use online banking, customers need to create an account with their bank and set up online banking services. This usually involves providing personal information, verifying identity, and creating login credentials. Once the account is set up, customers can log in to their online banking portal using their username and password. Some banks may also require additional security measures like two-factor authentication for added protection. After logging in, customers can view an overview of their accounts, including balances, transaction history, and pending transactions. They can also access other banking services like loans, credit cards, and investments.
Online banking allows customers to transfer funds between their own accounts or to other accounts within the same bank. They can initiate transfers by providing the recipient’s account details and specifying the amount to be transferred. It also, enables customers to pay bills electronically. They can set up recurring payments or make one-time payments to utility companies, credit card providers, or other payees.
Instead of receiving paper statements, customers can access their account statements online. These statements provide a detailed record of transactions, allowing customers to track their spending and manage their finances.
Online banking often offers additional services such as requesting new checks, ordering debit or credit cards, updating personal information, and contacting customer support.
Digital payments offer several advantages, such as instant transactions, easy record-keeping, and the ability to make payments remotely. They also provide enhanced security features, such as encryption and authentication measures, to protect sensitive financial information. The adoption of digital payments has been accelerated by advancements in technology, increased smartphone usage, and the growth of e-commerce. As a result, digital payments have become an integral part of the modern economy, transforming the way people transact and interact with businesses.